


Every day millions of companies around the world suffer huge losses to cyber-attacks targeted at enterprise computers and servers. This makes information security a top priority subject.
And the solution lies in moving your IT infrastructure to a protected environment.
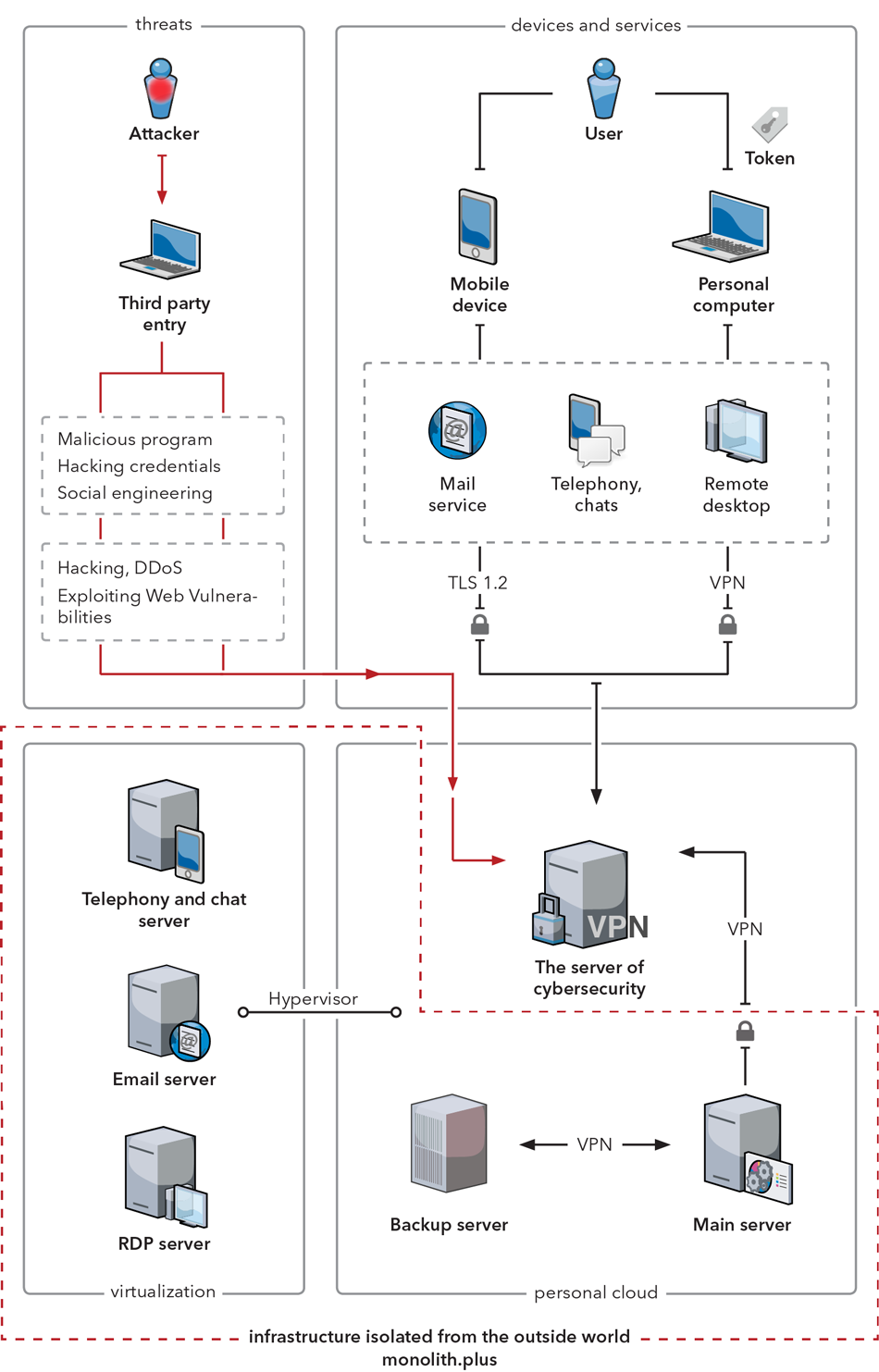
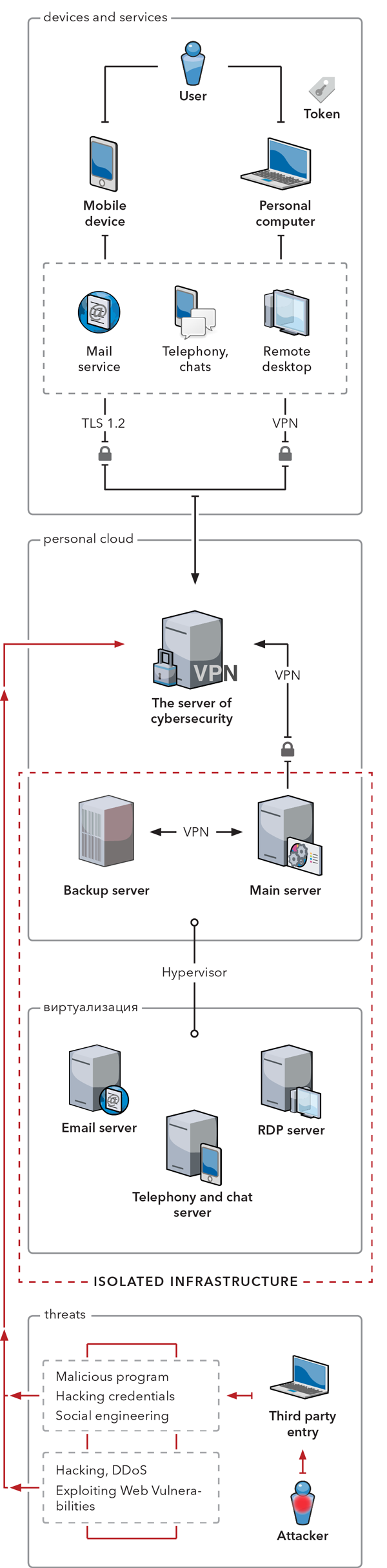
The server infrastructure is represented by three main parts: a firewall server, a main server, and a backup server.
Cybersecurity server (the firewall server) performs filtering of the processed traffic according to pre-configured rules. Its features include:
The main server is running all your software and services. This is where you store and manage your data.
The backup server creates copies of your data in the cloud storage. These copies can be used to restore data where it used to be or at a new location, in case of damage.
The server is responsible for:
In order to transfer data to the Firewall Server, the system uses a VPN (Virtual Private Network) method, which can establish one or multiple connections over another network.
The Firewall Server allows for:
To establish a PC — Firewall Server connection users must authenticate with a Token.
In order to ensure data security a TLS protocol is used providing:
All servers are interconnected with a VPN network. A reverse proxy technology is used to hide both the Main and Backup server’s IP addresses.
A Token is a compact device (a USB dongle) designed to ensure its owner’s security on the network.
The token is used for authentication purposes, as well as remote data access encryption.
All email and web servers, remote desktop, VoIP (voice-over-IP), cloud storages, and other enterprise applications are virtualized and hosted on the cloud server.
A cloud server is a technology for hosting and providing secure access to software and data over encrypted channels. Whatever stored in a cloud can be used by multiple PCs simultaneously
People may still confuse a ‘cloud server’ and a ‘cloud storage’. A cloud storage only hosts data, while a cloud server is capable of hosting operating systems, software and data. The virtual (cloud) server is the entity processing the data, leaving only the role of an endpoint terminal to the PC.
The main and backup servers collaborate with the virtual servers using a hypervisor.
In building and maintaining your IT infrastructure you can rely on your own skills, a full-time or outsourced IT engineer, or by obtaining an IaaS service from a dedicated provider.
IaaS (Infrastructure as a Service) is a service of renting out IT infrastructure to clients by its owner. This allows the customers to free up their IT capacity. All enterprise servers and networks are hosted by the provider. You still have the same IT resources but those are maintained by a 3d party.
Automated servers management along with their consolidation within a virtual framework reduces operating costs and minimizes risks and losses related to downtime and system vulnerabilities.
Main advantages of a virtual server:
You can migrate to a cloud in two ways: by building your own cloud infrastructure or subscribing to an IaaS service from a provider.
What about establishing your own data center where you can virtualize your services, the solution has a number of issues:
Moving your enterprise infrastructure to a 3d party cloud under an IaaS contract solves all the above problems. You can forget about all complications and have:
By building your own data center to cater only for the requirements of your company you are investing a significant amount of resources that will never return in a mediocre-quality IT infrastructure. A better solution would be to outsource this function to a company specializing in IT, which, in the end, is beneficial for both.
Today IaaS is capable of:
On the ground of a powerful and isolated hardware and software complex we are capable of deploying a secure cloud IT infrastructure of any level of complexity.
Our capacities allow you to host your own cloud storage, a remote desktop service, voice services, a mail server, messengers, and other applications your business may need.
Due to a resilient servers infrastructure and automatic software protection system we can ensure your data security and confidentiality 24/7.
Monolith Plus protects your data from all kinds of threats:
The transition to IaaS is your opportunity to establish a secure, reliable and flexible cloud infrastructure.


