


We offer a secure smartphone capable of anonymous use.
A smartphone that has sustained all the features and use case scenarios you are familiar with.
A smartphone that can hide your geographical location, routes you take, your contact lists and authentication history.
A smartphone that can restrict access to incoming and outgoing traffic, communication logs and voice mail.

The SIM card cannot be cloned.
Subsequently, all services where you authenticate with your mobile number remain accessible by you only.
Secure public messengers use,
e.g. Telegram or WhatsApp.
The smartphone has two isolated environments each with their own set of files and applications.
Access to your communication history, messages content, and voice mail is restricted.
You can make voice calls from any location on the planet, as long as you are connected to the Internet,
even where there are regulatory restrictions in place.
The smartphone is protected from covert listening, data interception, tracking your location or current user identification.
All files, passwords and communication history, both stored and transmitted, are protected
with triple encryption.

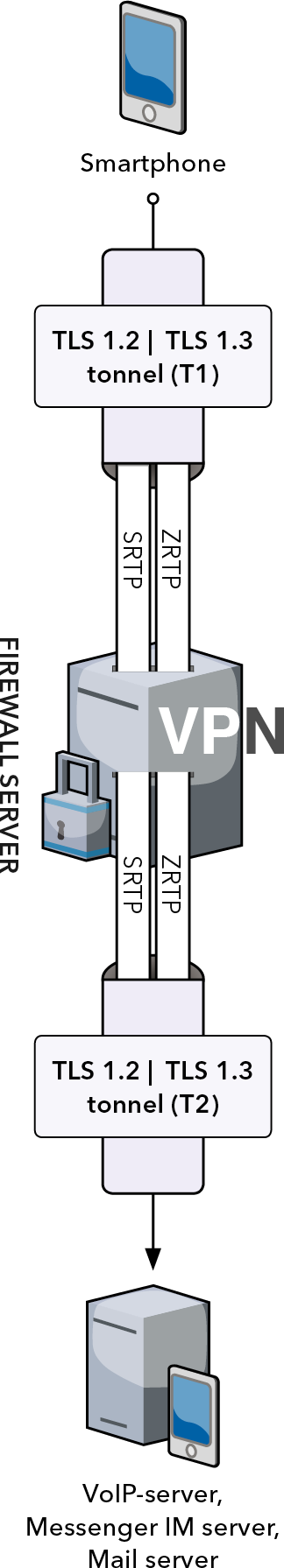
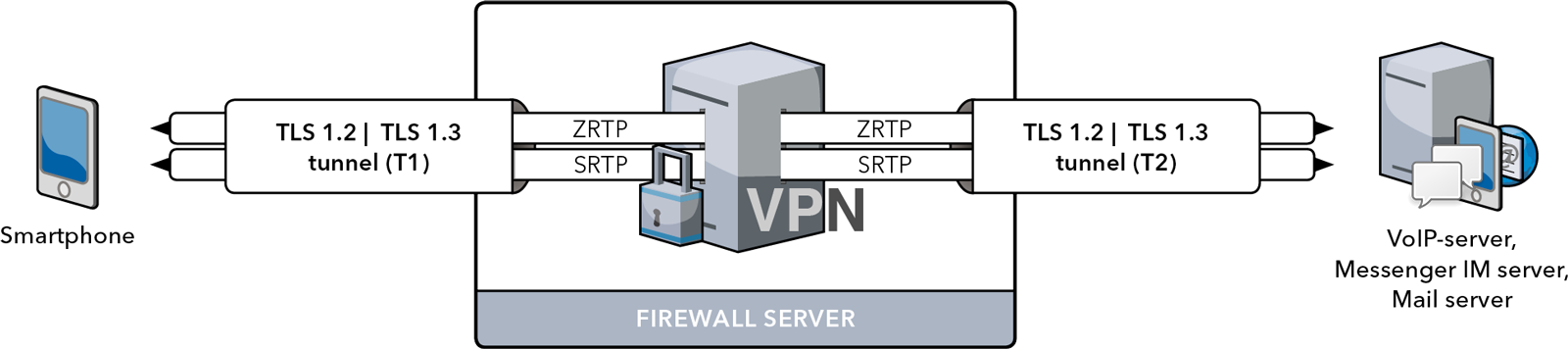
1. Using its IP address, the smartphone establishes a secure TLS 1.2/TLS 1.3 tunnel (T1) to the Cybersecurity server (Firewall server).
2. The data is encrypted and sent to the external IP address of the cybersecurity server.
3. The Firewall server forwards data to the VoIP server via another (T2) tunnel and that is where the data is decrypted.
While forwarding data from T1 to T2 the Firewall server inspects the packets and proxies the path to the VoIP server.
The Firewall server is transparent for the Smartphone.
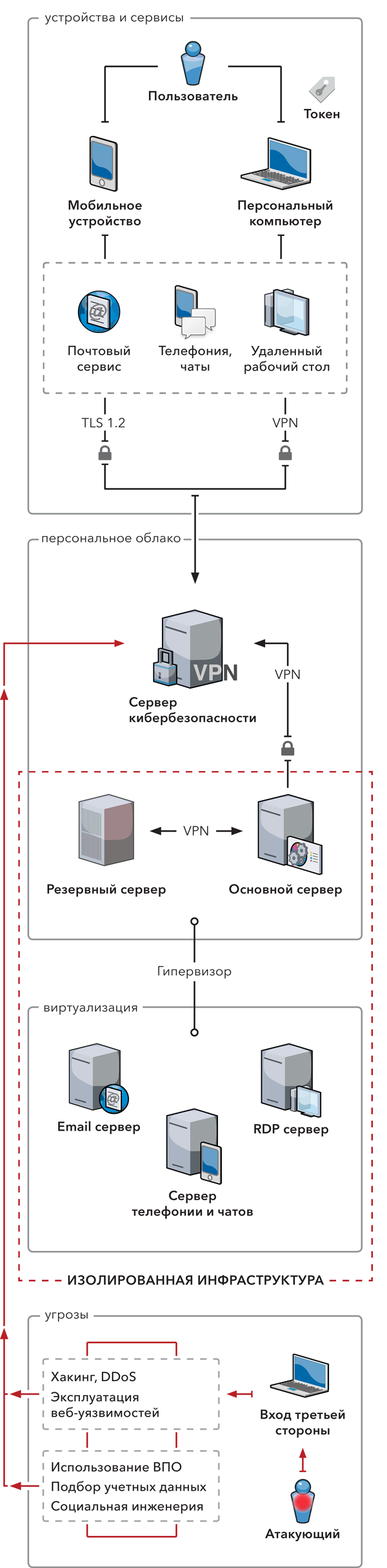
Сервер кибербезопасности устроен таким образом, что он незаметен для смартфона.
The cybersecurity server ensures the connection security. You cannot establish a non-TLS connection.
The Smartphone communicates to the open Internet resources via the server infrastructure which results in a secure and anonymous environment.
SRTP is a protocol that ensures message authentication, message integrity and prevents data spoofing.
ZRTP is a crypto protocol for encryption key negotiation used in Voice-over-IP networks.
Vulnerable on OS and application levels.
Vulnerable on centralized communication services level (VoIP, Messaging).
Vulnerable on hardware-level.
Vulnerable to GSM operator and ISP exploits.
Vulnerable on network level.
All communication channels use triple end-to-end encryption features.
We have added protection from hidden wires (or bugs) and data interception by mobile operators. All communication channels are encrypted, and your Internet usage is anonymous.
All communication and data exchange are handled by an isolated and managed by you only system.
Hardware-level espionage is eliminated in the Smartphone. The Smartphone has features storing your card details, fingerprints or passwords disabled.
We offer a secure mobile operating system free from spyware and data spoofing. You are in full control of all application permissions.
We offer a secure mobile operating system free from spyware and data spoofing. You are in full control of all application permissions.
Hardware-level espionage is eliminated in the Smartphone. The Smartphone has features storing your card details, fingerprints or passwords disabled.
All communication and data exchange are handled by an isolated and managed by you only system.
We have added protection from hidden wires (or bugs) and data interception by mobile operators. All communication channels are encrypted, and your Internet usage is anonymous.
All communication channels use triple end-to-end encryption features.


