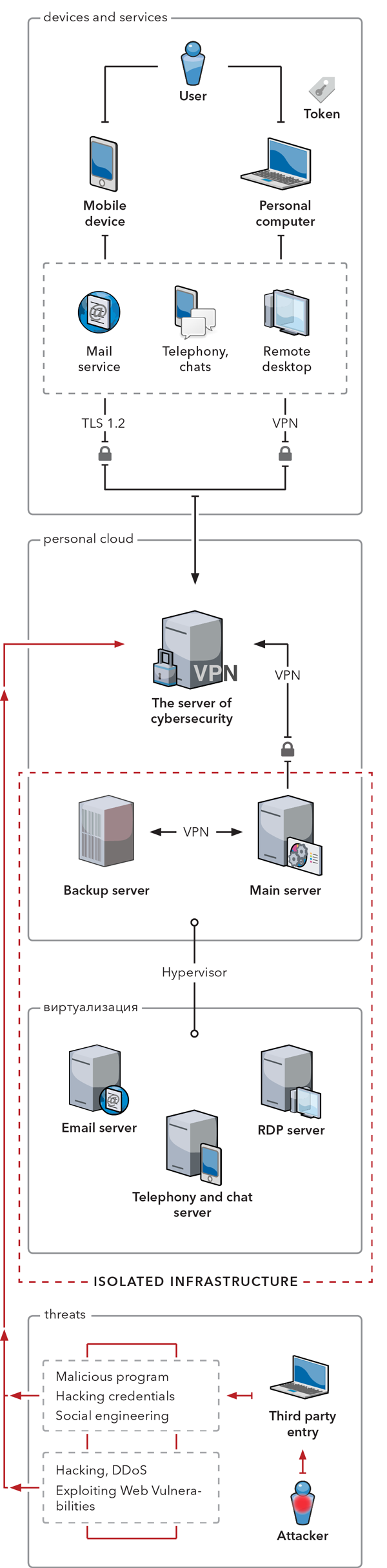
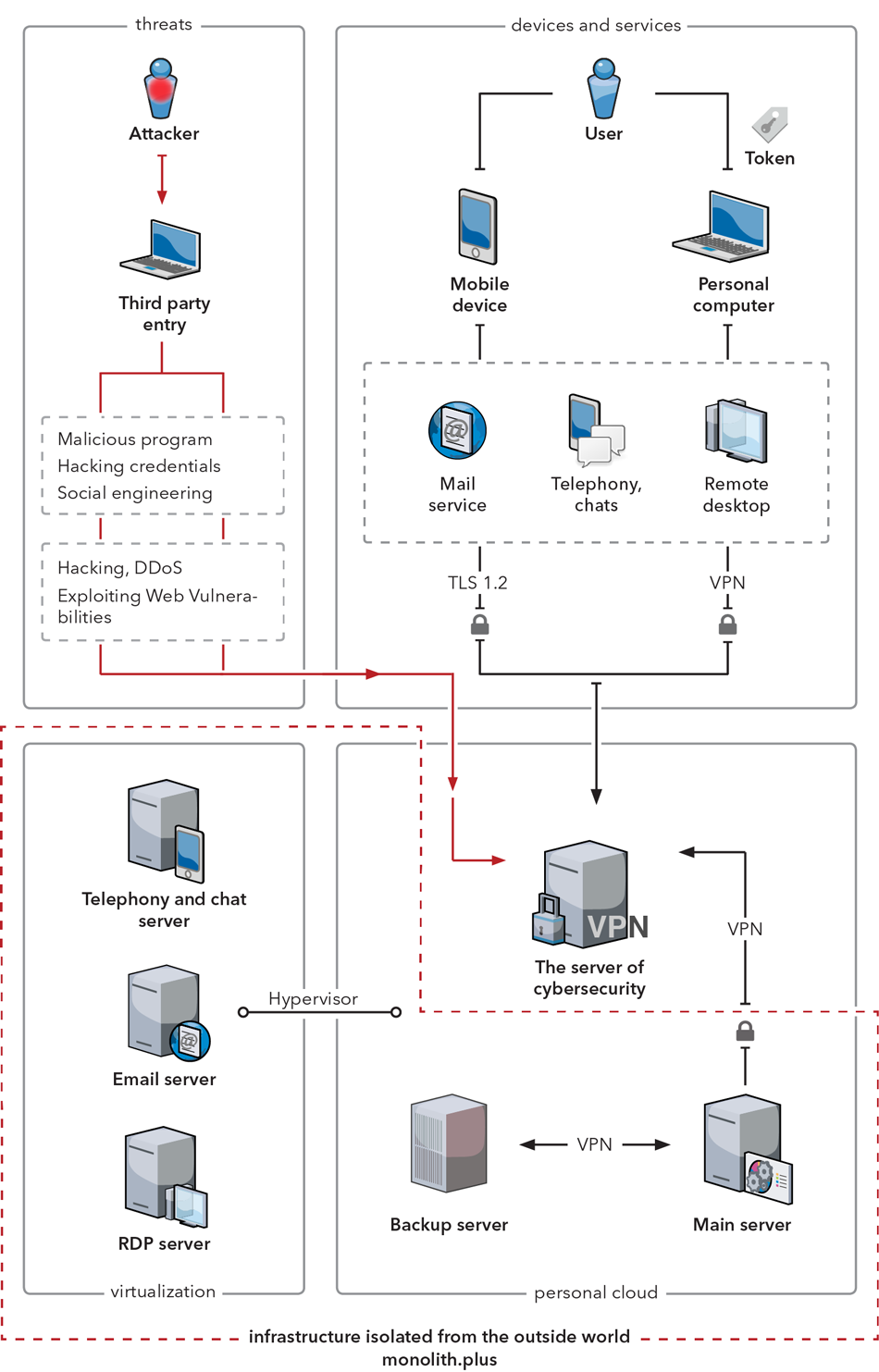
A personal cloud solution allows you to centrally store and manage your enterprise and confidential data, as well as protects it, eliminating the risks and subsequent profit loss due to data leakage and non-productive time.
Secure data access on the remote server. Token-based authentication. We help you move your data to a protected server environment because storing it locally has its drawbacks.
You can have your private instant messaging, telephony, and email services, hosted in a private protected infrastructure. That is how only you can access and manage your data.
Secure VoIP
Secure messaging
Secure email
Your PC is safe to work with your data on the device itself
All communication is protected with triple encryption
The Monolith Plus hardware and software complex:
Disables data theft both internally and by 3d parties
Restricts access to
your private data
Stops both legal and illegal methods of espionage
Allows uninterrupted
operation
Protects the infrastructure from malware
Excludes the possibility of data hijack by force
We offer an IT-threats protected smartphone capable of anonymous use.
A smartphone that has sustained all the features and use scenarios you are familiar with.

The smartphone has two isolated environments with their own sets of files and applications.
It protects access to your conversations history, calls and voice mail.
The smartphone is protected from covert listening, data interception and tracking.
All files, messaging logs are encrypted both when stored and in transmission.
You can place calls from anywhere, as long as you are connected to the Internet.
No limitations.
Example of building a secure cloud infrastructure.
We offer an encrypted laptop with two independent operating systems.
Data is secure while locally on the laptop as well.

Two isolated work environments plus a hidden volume
OS choice is defined by the authentication scenario. For example, one password takes you to the main OS, another one – to the guest OS.
Remote desktop
You authenticate with a token to work with your data on a remote server.
Encrypted operating systems
Per-volume encryption makes them invulnerable to hacking attempts.
Token-based authentication
The token serves both the authentication and encryption purposes.
IC laser motion sensor
Controls the laptop position. When lifted from the table, the system will automatically shut down.


