


We offer an encrypted laptop with two independent work environments. It also enables secure storage for your data on the computer itself.

Two isolated systems plus a hidden volume
How you log in defines where you find yourself. For example, one password takes you to the main system, another password to the guest system.
Remote desktop feature
You work with a remote server where you authenticate with a token.
Encrypted operating system
Per-volume encryption make data invulnerable to hacking attempts
Token-based authentication
You use a token to authenticate and to encrypt your data
IC laser motion sensor
Controls the laptop position. When lifted from the table, the system will automatically shut down.

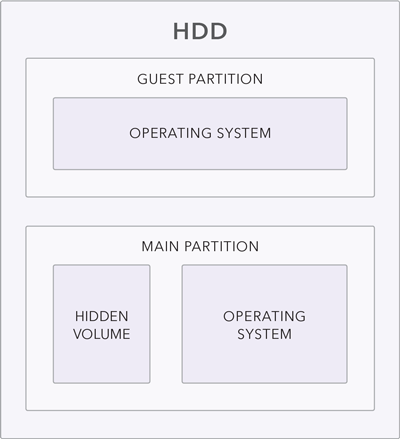
The local disk drive is split into two partitions and both are encrypted.
Main partition carries an operating system and a hidden volume. You can access the hidden volume from the guest environment, but it will look like an empty storage, hiding the main partition.
The guest partition is running its own operating system and is encrypted as well but provides only basic features.
The system uses XTS-mode 14-round AES algorithms with 256-bit keys (AES-256). XTS is a cutting-edge mode for AES providing better encryptions that ECB or CBC.
In XTC mode, header and secondary header keys are generated using PBKDF2 with a 512-bit salt at 327661 to 655331 iterations, depending on the hash function.
The keys and algorithms guarantee strong resistance to cryptanalyses from 3d parties.


